Using Tailscale For Homelab VPN Connectivity
What is Tailscale?
Tailscale is a VPN service that makes the devices and applications you own accessible anywhere in the world, securely and effortlessly. It enables encrypted point-to-point connections using the open source WireGuard protocol, which means only devices on your private network can communicate with each other.
I am using Tailscale for VPN on my all devices. My pfsense is installed Tailscale package that is set up as an exit node and advertises my home network. 
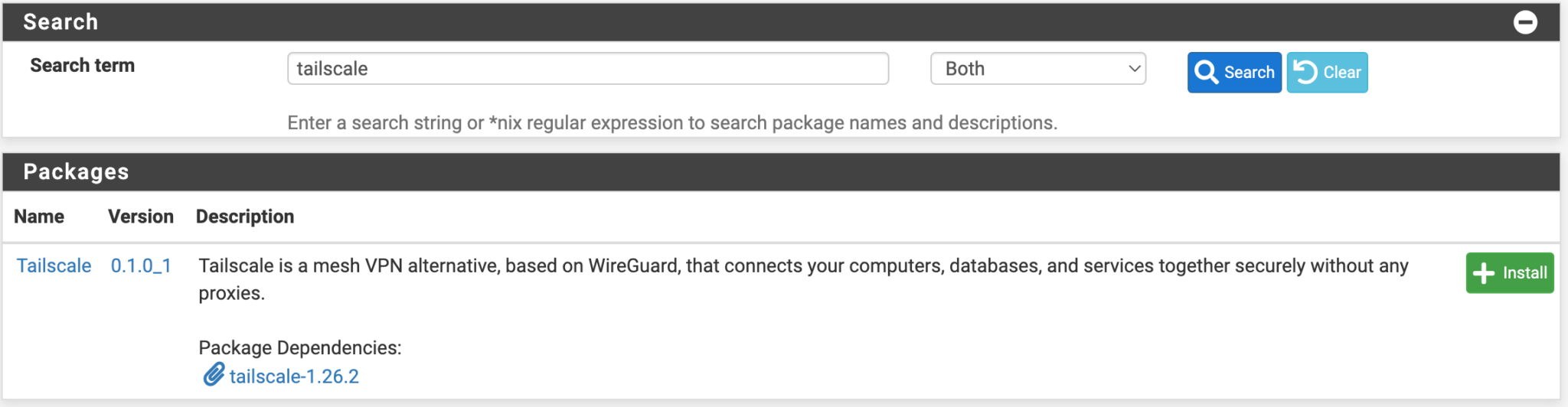
Set Up Tailscale on pfSense
Select VPN, then Tailscale to launch the Tailscale settings.
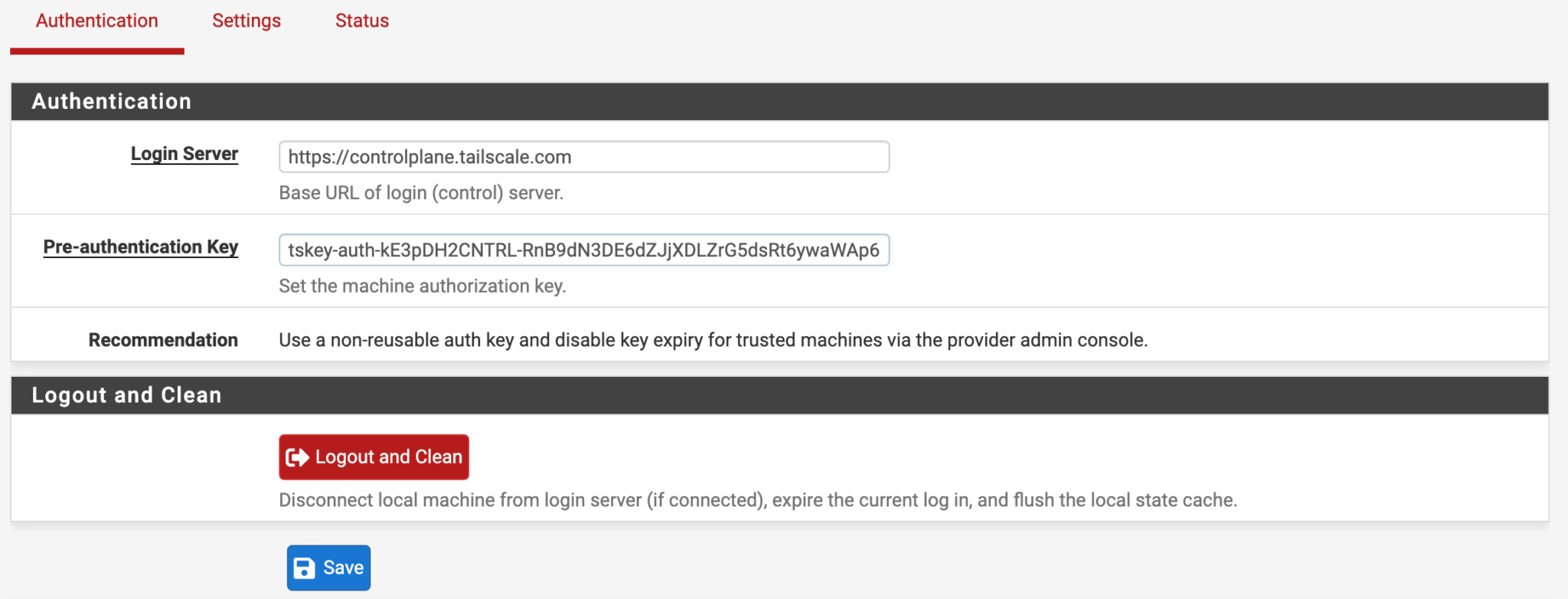
At this point, we need to configure the pre-authentication key. This can be created on the Tailscale website. If you don’t already have an account, create one, then log in and select Settings, then Keys.
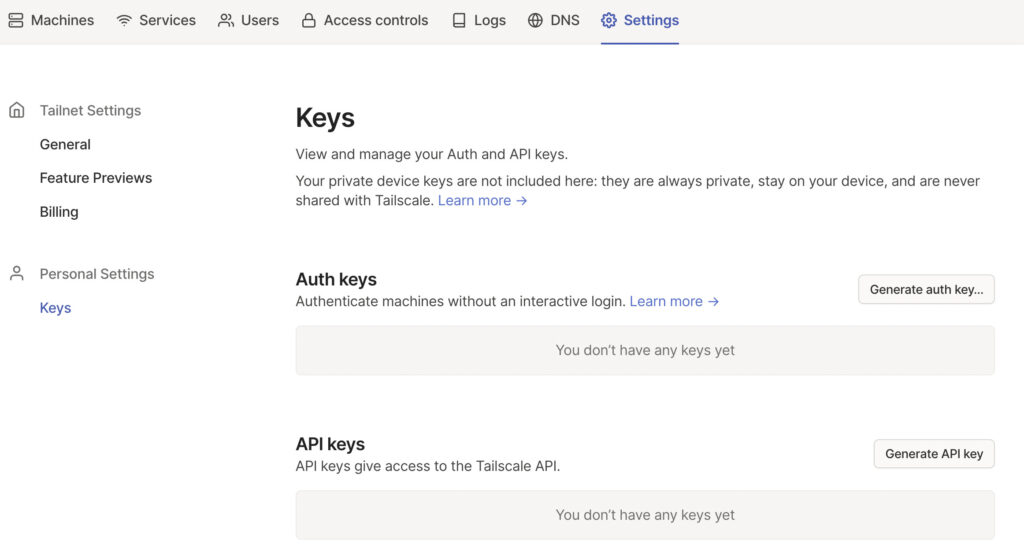
Select generate auth key so that we can create the key for pfSense. Select Generate Key (the settings can stay as default).

After the key has been generated, copy it, then go back to the Authentication section of Tailscale on pfSense.

After saving, select Settings, then enable Tailscale and Save.

Exit Node
Inside the Tailscale settings on pfSense, enable the offer to be an exit node for outbound internet traffic from the Tailscale network option. Also, set the Advertised Routes as your local subnet, then save.

On the Tailscale website, select Machines, then Edit Route Settings.
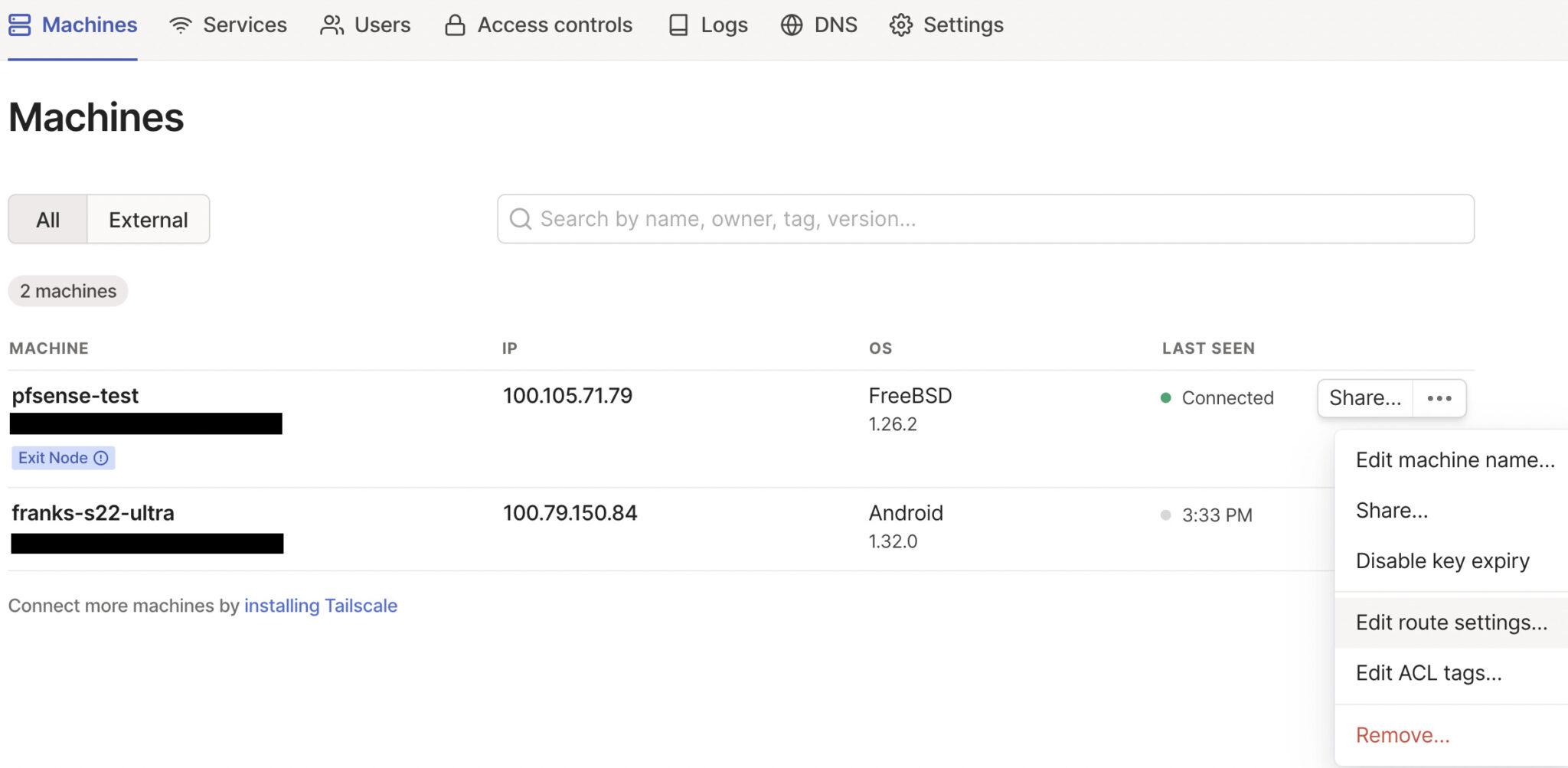
Approve all subnet routes and Select use as exit node. The exit node functionality is now set up and can be used by client devices.

Select the DNS tab, you can set your local DNS server as Global namesever and override it.(if you have pihole, you can set the pihole’s ip in there.)
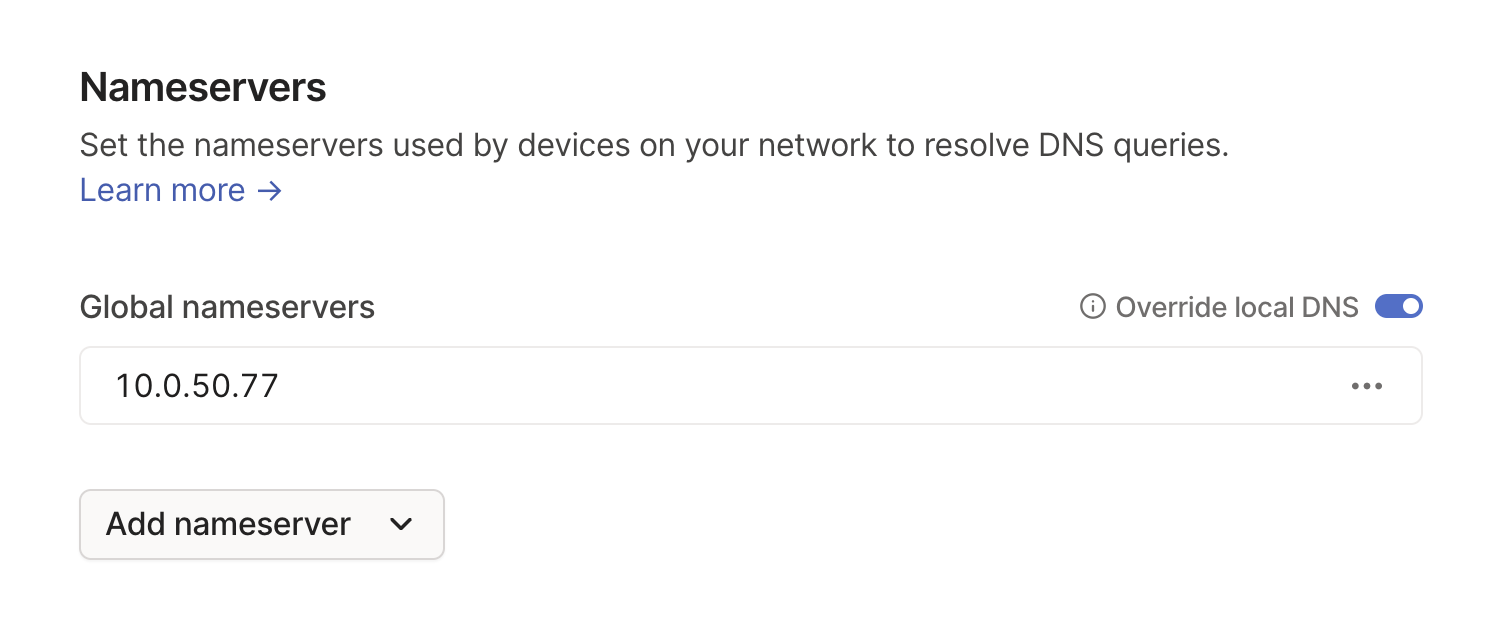
Tailscale is now configured! You can now add other devices or simply connect to Tailscale from an external network to access all of your local devices.
Cli command
1
sudo tailscale up --advertise-routes=10.0.0.0/24,10.0.1.0/24
Advertise the device as an exit node
1
sudo tailscale up --advertise-exit-node